-
The $285 Billion “Markdown Meltdown”: How a Few Text Files on GitHub Shook the Global Stock Market
In late January 2026, Anthropic quietly released something that looked utterly harmless: a set of open-source plugins for their Claude Cowork tool. No flashy keynote, no billion-dollar acquisition announcement—just a GitHub repository filled with Markdown files, JSON configs, and simple instructions. By early February, roughly $285 billion in market value had evaporated from software, legal…
-
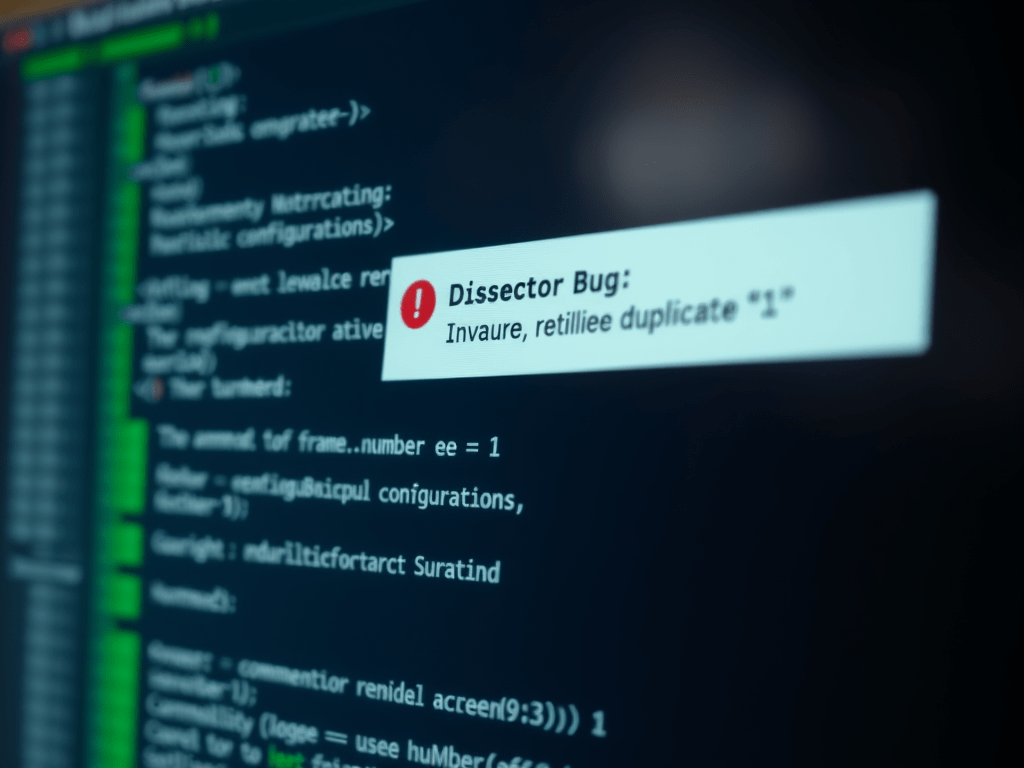
Resolving Wireshark Dissector Bug: Invalid Leading, Duplicated, or Trailing Space in Filter Name on Kali Linux
Article ID: KB-WS-001 Last Updated: December 16, 2025 Applies To: Wireshark 4.x on Kali Linux (Debian-based distributions) Severity: Medium (Prevents Wireshark from launching) Symptoms When launching Wireshark on Kali Linux, you encounter the following error dialog: This error appears immediately upon startup and is often triggered after system updates (e.g., apt upgrade). The filter frame.number…
-
Why Failover, Observability, and High Availability Didn’t Prevent the October 2025 AWS US-EAST-1 Outage
Why Failover, Observability, and High Availability Didn’t Prevent the October 2025 AWS US-EAST-1 Outage
-
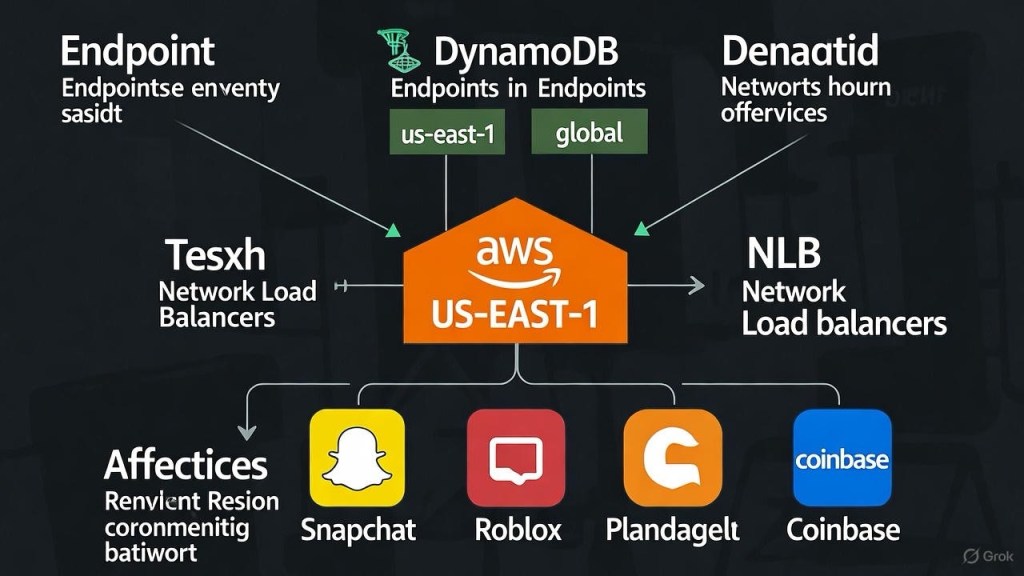
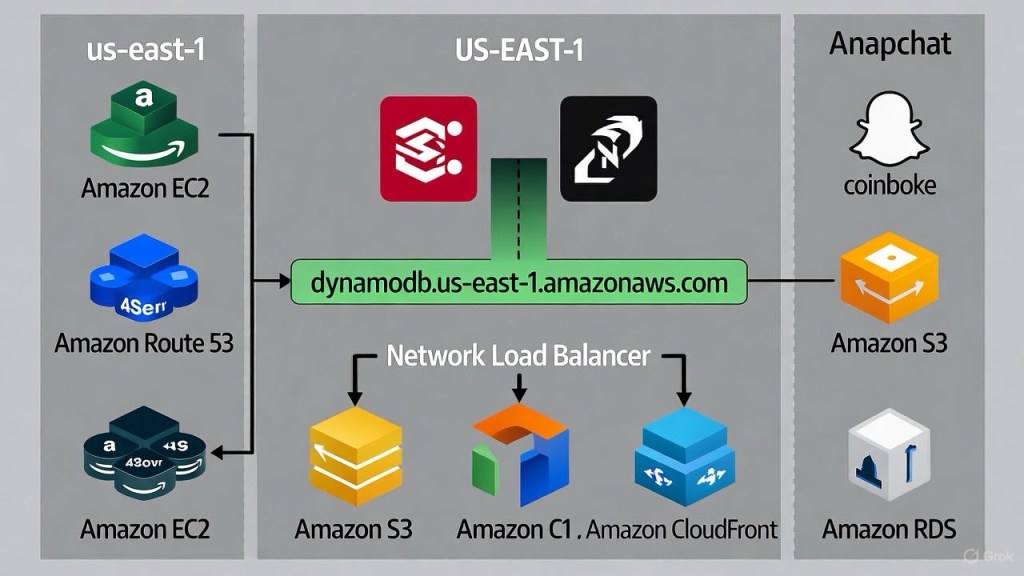
The AWS DynamoDB Domino Effect: Unpacking the October 2025 US-EAST-1 Outage
Blog Post Summary: AWS US-EAST-1 Outage Architecture Overview (October 20-21, 2025) Dive into the recent AWS outage that shook the US-EAST-1 region, disrupting services like Snapchat, Roblox, and Coinbase. This post breaks down the architecture behind the failure, highlighting DynamoDB endpoints and network load balancer issues, and provides a detailed diagram for clarity. Explore the…