-
Lab 10 : SQL injection attack, listing the database contents on Oracle
Problem Statement : This lab contains an SQL injection vulnerability in the product category filter. The results from the query are returned in the application’s response so you can use a UNION attack to retrieve data from other tables. The application has a login function, and the database contains a table that holds usernames and passwords. You…
-
Lab 9 : SQL injection attack, listing the database contents on non-Oracle databases
Problem Statement : This lab contains an SQL injection vulnerability in the product category filter. The results from the query are returned in the application’s response so you can use a UNION attack to retrieve data from other tables. The application has a login function, and the database contains a table that holds usernames and passwords. You…
-
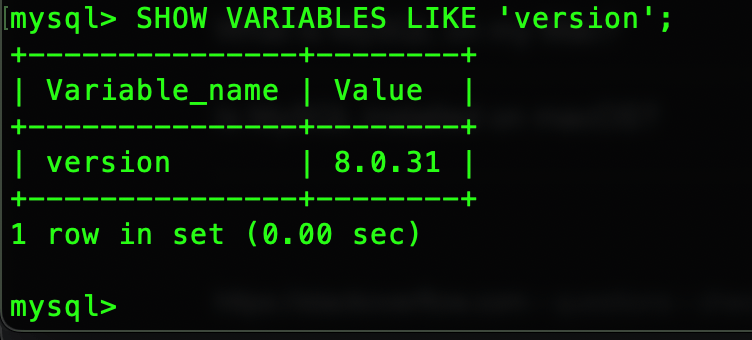
LAB 8 : Lab: SQL injection attack, querying the database type and version on MySQL and Microsoft
Problem Statement : This lab contains an SQL injection vulnerability in the product category filter. You can use a UNION attack to retrieve the results from an injected query. To solve the lab, display the database version string. REQUIREMENT IS – Make the database retrieve the string: ‘8.0.31-0ubuntu0.20.04.2’ Understanding: Different Database Syntax Database versions: You can query…
-
Lab 7 : SQL injection attack, querying the database type and version on Oracle
Problem Statement : This lab contains an SQL injection vulnerability in the product category filter. You can use a UNION attack to retrieve the results from an injected query. To solve the lab, display the database version string. Requirements : Make the database retrieve the strings: ‘Oracle Database 11g Express Edition Release 11.2.0.2.0 – 64bit Production, PL/SQL…
-
LAB 6: SQL injection UNION attack, retrieving multiple values in a single column
Problem Statement : This lab contains an SQL injection vulnerability in the product category filter. The results from the query are returned in the application’s response so you can use a UNION attack to retrieve data from other tables. The database contains a different table called users, with columns called username and password. To solve the lab, perform an SQL…